The Simple
Lightning Newsletter
How Do Payment Channels Make Up The Lightning Network? - #2 Hashlocks
This the second post in our 3-part introductory series on payment channels.
In the last deep dive, we talked about how a 2-of-2 multisig is used to move bitcoin off of the main chain and into a payment channel. In this post we’ll go into how payments can be routed though multiple payment channels in the Lightning Network.
Payment Channel Basics:
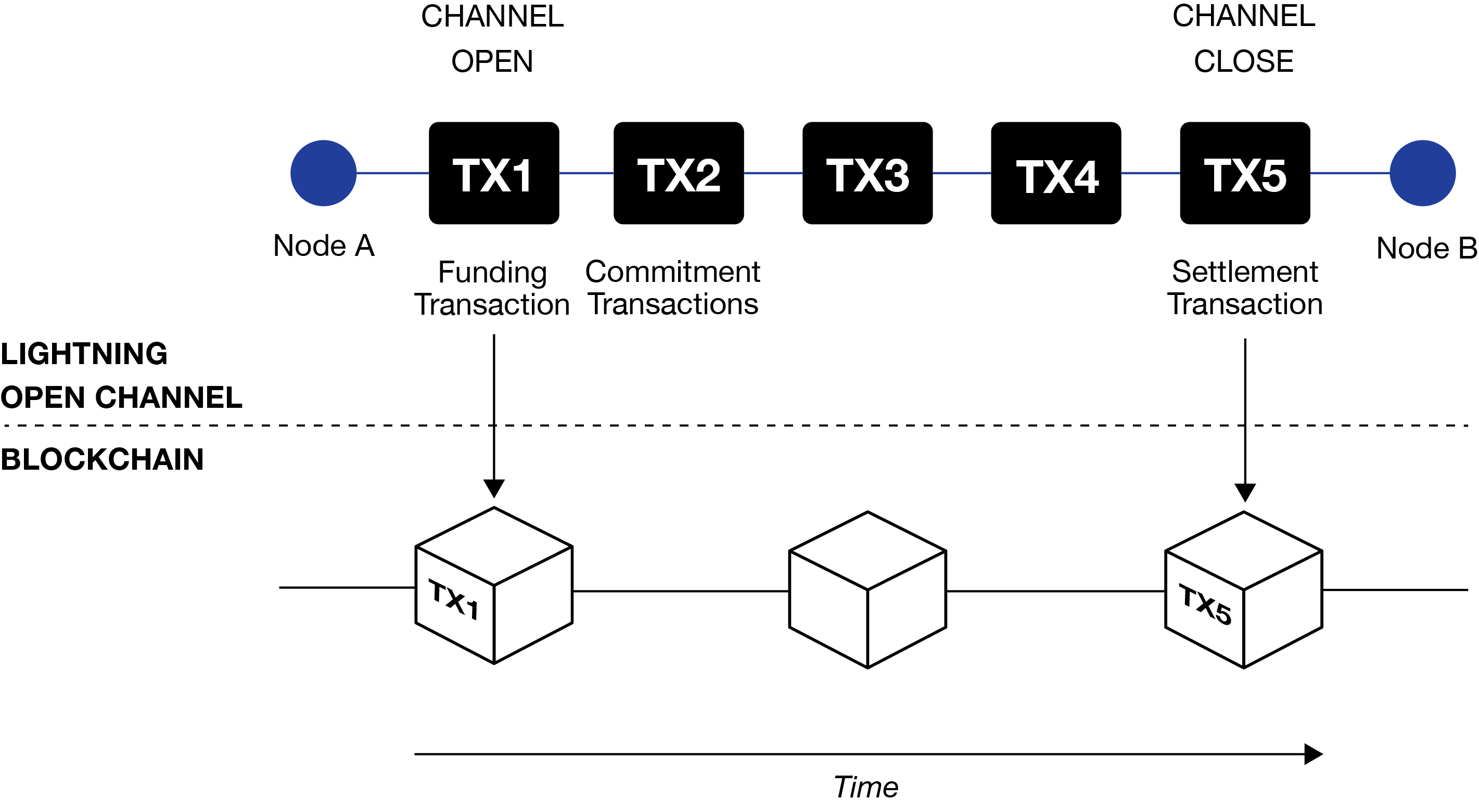
Users and businesses on the network operate as lightning nodes, two nodes can transact peer-to-peer to move funds in a payment channel between them without having to incur fees that may one day become prohibitive on the Bitcoin blockchain.
But one peer-to-peer payment channel in isolation is not much of a network.
How are payment channels connected to create the full Lightning Network?
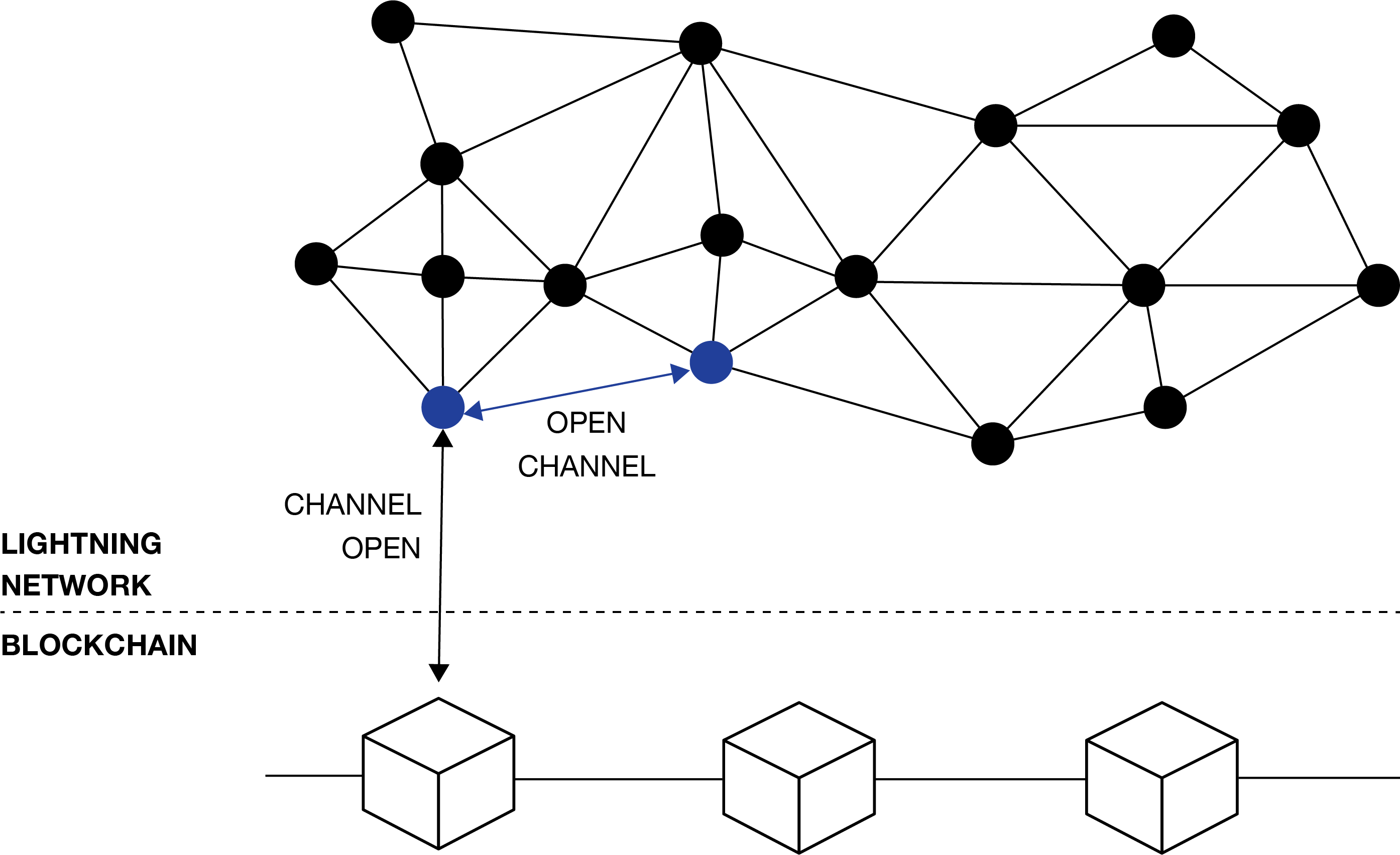
Peer Connections and Channels
Nodes talk to each other through the TCP/IP layer of the internet, and connect to each other by establishing payment channels on the Lightning Network. Although you can open as many channels as you want, every open channel costs some amout of on chain fees, and requires tieing up some liquidity.
On the Lightning Network, users don’t need to open a channel with every user they want to transact with, because transactions can be routed through other peers.
But how do payments route through nodes across the network?
Routing and Receiving Payments
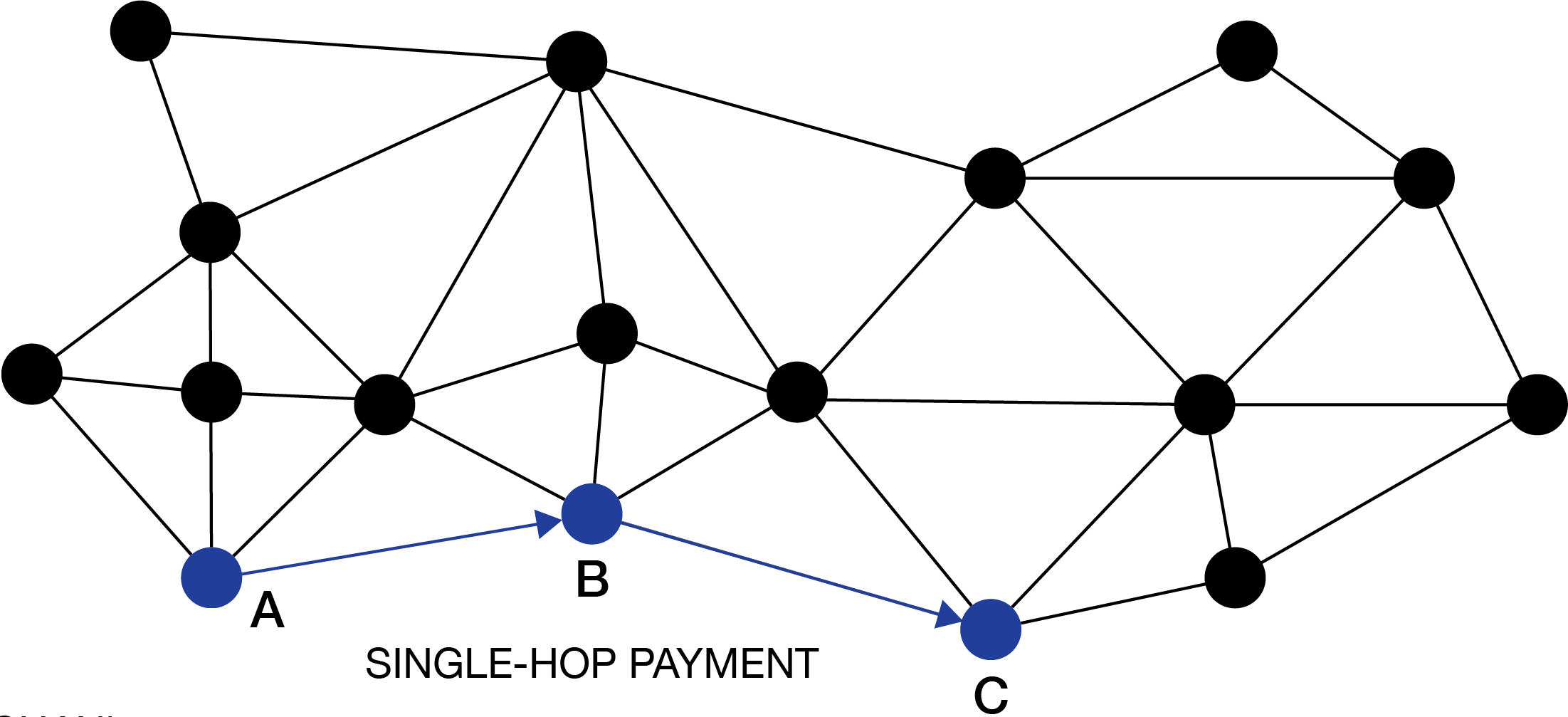
Say Node A in the A-B-C connection wants to send 100k Sats (or about $50) to Node C with 1 hop in the route (Ct. Fig. 4).
How does the protocol enable the payment to go through the middle man (Node B) trustlessly?
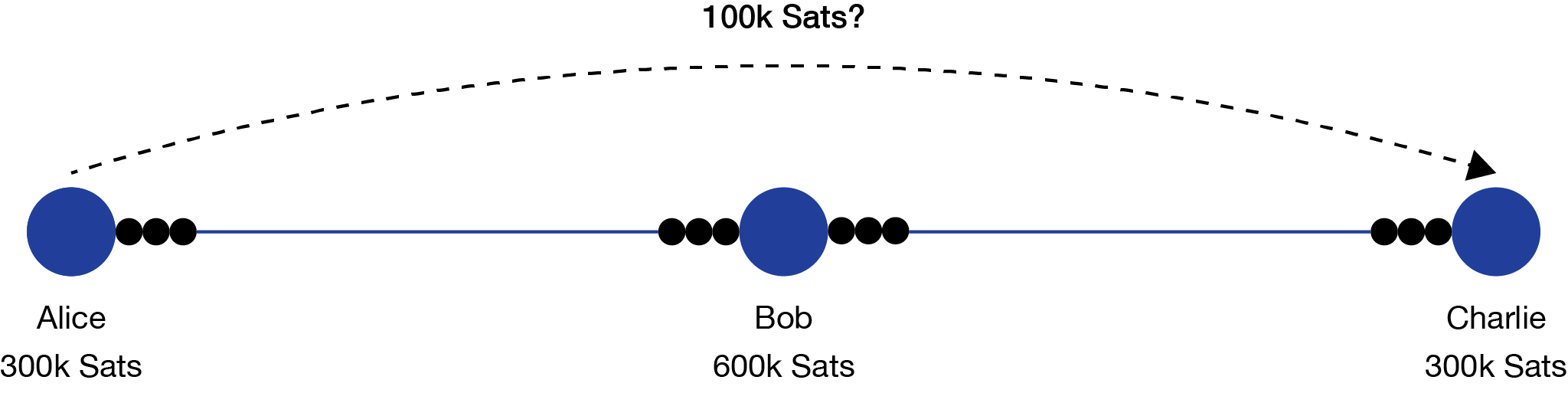
Alice can’t blindly trust Bob to pass the payment to Charlie without putting some security measures in place first.
What is a Hashlock?
In Bitcoin hashes are used in a variety of different ways, full nodes use it to validate data, link together blocks in the chain, and miners use it to prove they’ve done work for the rest of the network. In this instance, hashes are used to create a lock.
A hashlock is a cryptographically hashed or scrambled random number:
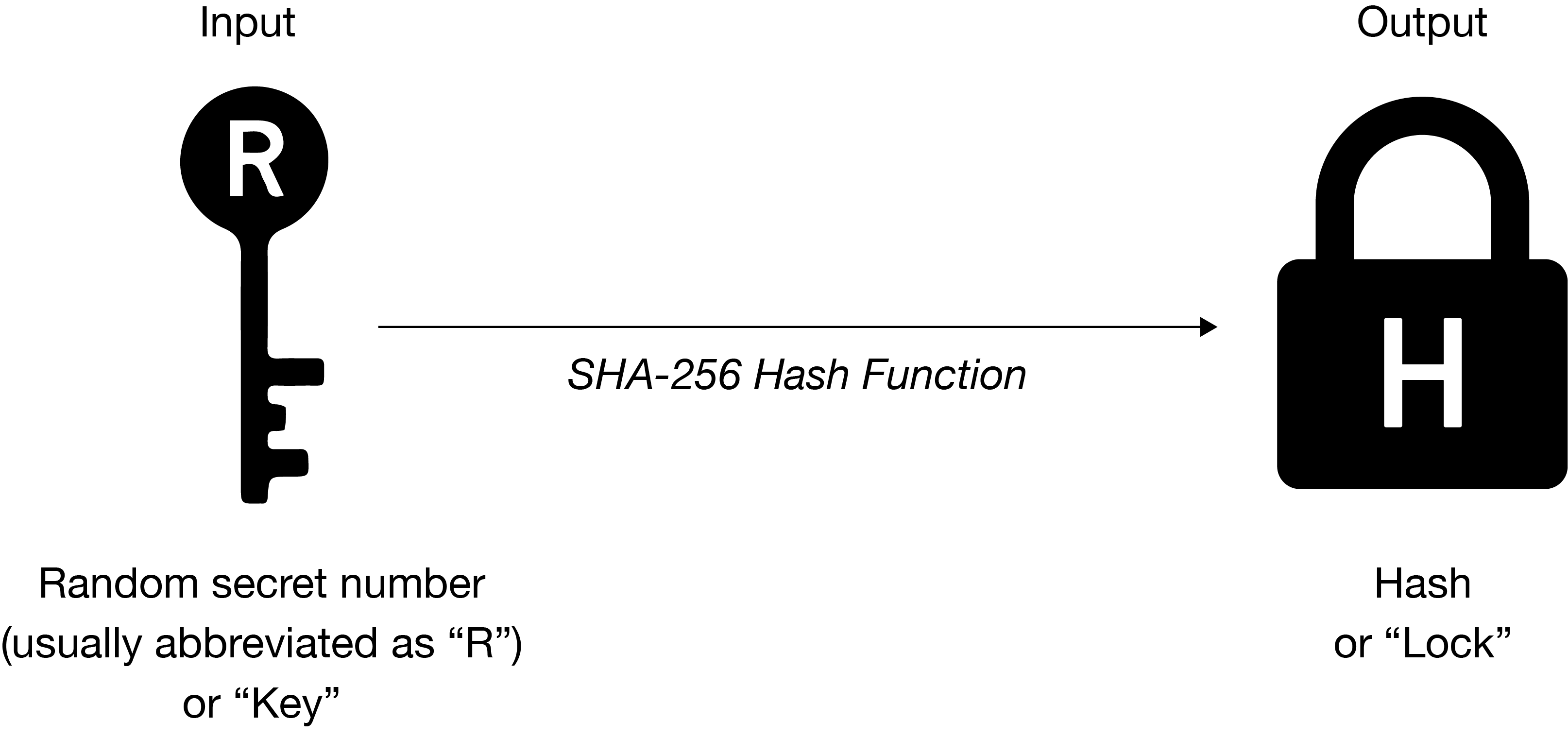
SHA-256 is a one-way mathematical hash function that creates an unique output. We can mathematically prove that it’s impossible to guess or reproduce the original number from the output hash. Because of this property, the hashed output can function as a lock, and the original input can serve as the key.
The user that generated the lock can give it to other users for the purpose of locking up bitcoin. To unlock the bitcoin, the user just provides the secret key. Revealing the key in a transaction, shows everyone how to reproduce the unique hash.
Trustless Payments Channel Routing With HTLCs
Here the specific hashlock being used is called an HTLC. Hash Time Locked Contracts (HTLCs) are conditional payments used in payment channels, and are the fundamental building blocks of every payment on the Lightning Network.
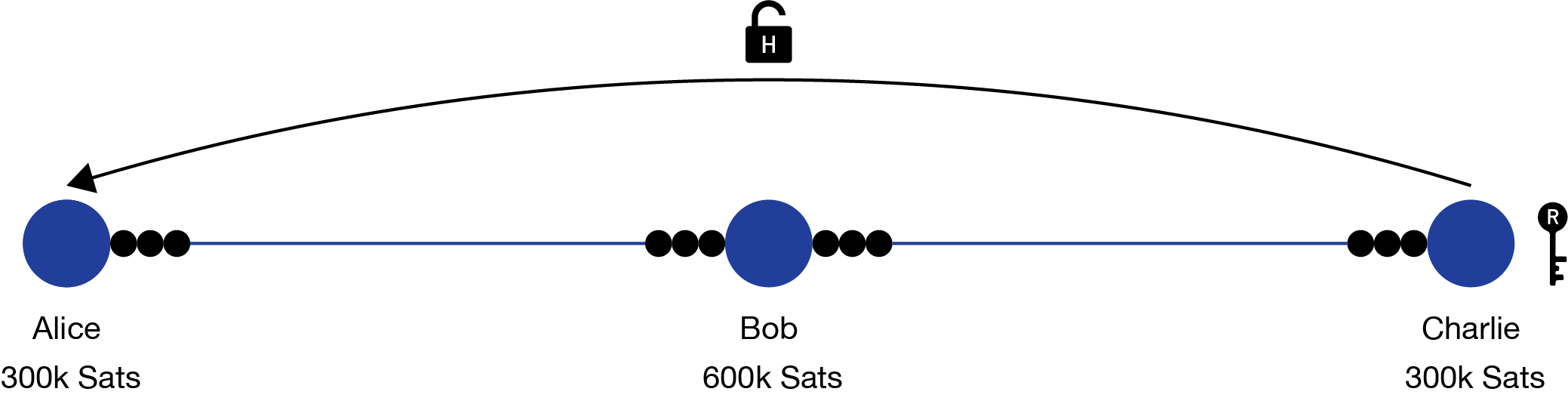
Sticking with this example, Alice wants to send 100k Sats to Charlie, but the two of them don’t have a direct channel relationship, and it’s more bitcoin than either of them want to spend to open a new channel. Conveniently, they both have 300k Sats channels with Bob, so the payment can route through him.
- First, Charlie generates a random number as the secret key and computes its SHA-256 hash represented as the lock. Then he sends the hashlock to Alice.
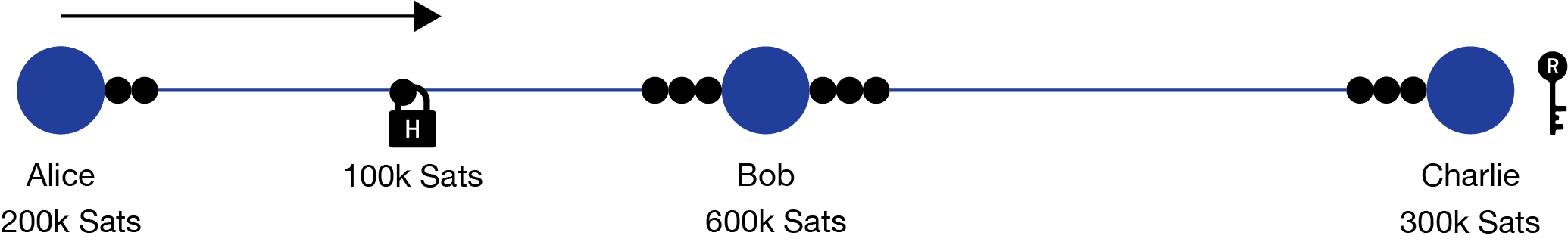
- Alice uses her payment channel with Bob to pay him 100k Sats, but she adds the condition that the key for Charlie’s hashlock is needed to claim the funds. In order for Bob to claim the payment, he has to provide the secret data which was used to compute the hash.
- Bob keeps his payment from Alice, and generates his own 100k Sats payment to Charlie. Using the hash provided from Alice Bob locks his 100k Sats payment, creating the condition that the key is needed to claim the funds. Using his payment channel to Charlie, Bob sends the payment along.
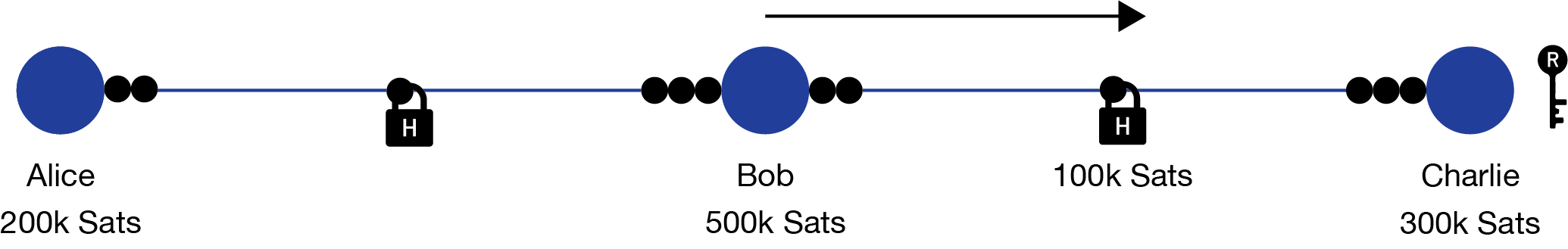
- Charlie has the original key (usually called the preimage) that was used to produce the hash, so when Charlie receives the payment from Bob he’s able to lock and claim the funds. By making this transaction the secret is revealed to Bob, so that he can also claim his payment from Alice.
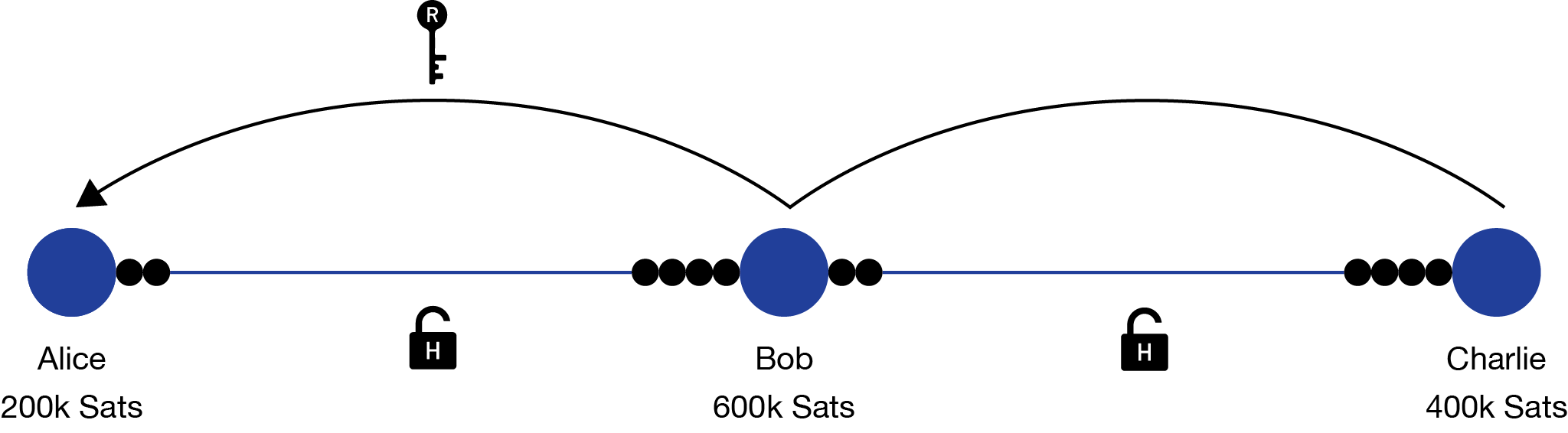
With HTLCs the capacity of each of the two channels don’t change, only move from peer-to-peer. The purpose of HTLCs is to make atomic payments, so that the peer-to-peer transaction isn’t divisible into separate parts.